Reimagining Personal Property Rights in the Digital Age: The Case for Data Ownership
Personal Data Ownership Act
As society rapidly advances into the digital era, the concept of personal property is evolving beyond physical assets to encompass the vast amounts of data generated by individuals. In an age where browsing history, clicks, location data, and shopping habits are meticulously collected by corporations, the need to reassess personal property rights in relation to data is more pressing than ever.
The Modern Dilemma: Data as Personal Property
Traditionally, personal property rights have been well-defined, encompassing physical goods and real estate. However, the rise of digital technology has introduced a new dimension of personal assets: data. Every interaction online—whether it’s a search query, a social media post, or a purchase—generates data that companies eagerly collect and analyze. This data is valuable, often forming the basis for highly profitable business models.
Yet, despite its intrinsic value, individuals typically have little control over their own data. Companies accumulate vast quantities of personal information, using it to target advertisements, influence purchasing decisions, and even make critical business decisions. This imbalance raises a fundamental question: Shouldn’t individuals have ownership over their own data?
The Right to Control and Profit
The argument for data ownership is grounded in the principles of personal autonomy and property rights. Individuals should have the absolute right to review, edit, or delete any information that corporations collect about them. This control ensures that personal data remains accurate and secure, reducing the risk of misuse or exploitation.
Furthermore, individuals should have the right to profit from the sale or transfer of their data. Just as one can sell a physical asset, personal data should be treated as a commodity that individuals can monetize if they choose. This shift would not only empower individuals but also foster a more equitable digital economy where the benefits of data collection are shared.
Proposed Legislative Framework
To address these concerns, a comprehensive legislative framework is needed to safeguard data ownership rights. The proposed “Personal Data Ownership Act” aims to establish clear guidelines for data control:
Title: Personal Data Ownership Act
Section 1: Short Title and Alternate Title
- Short Title: This Act shall be known as the “Personal Data Ownership Act.”
- Alternate Title: This Act may also be referred to as the “I Own Me” Act.
Section 2: Purpose The purpose of this act is to return ownership of data collected about a person to the person who’s data is being collected.
Section 3: Definitions
- Personal Data: Any information relating to an identified or identifiable natural person, including but not limited to biometrics, physical location history, internet browsing history, shopping history, Personally Identifiable Information (P.I.I.) as defined in other statutes, associations with other persons, video and audio recordings, and other biometric and DNA information. Collecting data from a device, that can be associated to a data subject, is the same as collecting data from a person (ie: personal data).
- Data Collector: Any entity, public or private, that collects, processes, or stores Personal Data.
- Data Subject: An individual whose Personal Data is collected, processed, or stored by a Data Collector.
- Electronic Device: Any electronic device that can be used for the collection of data on an individual, including but not limited to computers, smartphones, tablets, wearables, and IoT (Internet of Things) devices.
Section 4: Personal Data Ownership
- Ownership Rights: Every individual shall have personal ownership of all Personal Data collected about them, regardless of the nature of their relationship with the Data Collector. Ownership rights include:
- History of location.
- History of search activity.
- History of clicks, actions, motions, or scrolls, or any other device measurements.
- Personally Identifiable Information (P.I.I.) as defined in other statutes.
- Video and audio recording information.
- Other biometric and DNA information.
- Control Rights: Data Subjects shall have the authority to review, edit, or remove their Personal Data, in whole or in part, at any time.
Section 5: Right to Review and Edit
- Access to Data: Data Collectors must provide Data Subjects with access to all Personal Data collected about them upon request.
- Correction of Data: Data Subjects shall have the right to demand correction of inaccurate or incomplete Personal Data.
- Deletion of Data: Data Subjects shall have the right to demand the deletion of their Personal Data, in whole or in part, except as provided in Section 6.
- Non-Retaliation: A Data Collector, or a company that contracts with a Data Collector, may not cancel a person’s membership or ability to use a service due to a person requesting that their information be removed.
Section 6: Data Collection and Usage
- Transparency: Data Collectors must inform Data Subjects about the collection and use of their Personal Data, including the purposes for which it is collected.
- Consent: Data Collectors must obtain explicit consent from Data Subjects before collecting or processing their Personal Data.
- Parental Consent: No data may be obtained about a person under the age of 13 without parental consent.
Section 7: Exceptions
- Device Data Collection: This act does not apply to a device that does not store Personal Data for more than 24 hours or transmit that information to another device for storage.
- Governmental Data: This Act does not apply to Personal Data collected, processed, or stored by government entities for official purposes.
- Medical Data: This Act does not apply to Personal Data collected, processed, or stored by medical entities for the purposes of diagnosis, treatment, or healthcare management. This Act does not apply to individuals who are under the medical supervision of another.
- Employment Data: This Act does not apply to Personal Data collected, processed, or stored by employers for employment-related purposes.
- Law Enforcement Data: This Act does not apply to Personal Data collected, processed, or stored by law enforcement agencies for the purposes of criminal investigation, incarceration, public safety, or national security.
- Security of Persons or Property: This Act does not apply to surveillance (video and/or audio) of a person or property conducted to protect against theft, vandalism, or violence.
- Public Spaces: This Act does not restrict the constitutional right to record (video or audio) individuals in public places where there is no expectation of privacy, as long as such recording complies with applicable laws regarding privacy and consent.
- Journalistic Exemption: Journalists and media organizations shall be permitted to gather Personal Data on individuals for newsworthy stories that serve the public good, provided that such data collection is conducted in accordance with applicable laws and ethical standards for journalism.
- Personal and Family Data: This Act does not apply to individuals who collect and store data or documents solely for themselves or their immediate family.
- Ancestral Information: This Act does not apply to the retention of information related to ancestral or genealogical research.
Section 8: Enforcement and Penalties
- Enforcement Authority: The designated regulatory authority shall have the power to enforce the provisions of this Act.
- Penalties for Non-Compliance: Data Collectors found in violation of this Act shall be subject to penalties, including fines and corrective actions as determined by the regulatory authority. An individual may also sue the Data Collector in Civil Court. A plaintiff shall not be required to prove monetary damages to bring a case or have that case adjudicated.
- Class A Misdemeanor: It shall be a Class A Misdemeanor for any person to collect or store data on an individual without their knowledge.
- Corporate Responsibility: When the offender is a corporation, the highest officer of that corporation shall be held responsible for the actions of the corporation and subject to penalties as specified for individual offenders.
- Defense Against Prosecution:
- It shall be a defense against prosecution if a Data Subject has signed an authorization for the collection of data, provided the data to be collected is plainly spelled out as to what is specifically collected.
- It shall also be a defense against prosecution if the information collected is public knowledge or readily available from public sources.
Section 9: Transfer or Selling of Data
- Authorization Required: Data Collectors must seek explicit authorization from the Data Subject prior to transferring or selling their Personal Data to any third party.
- Disclosure of Terms: Data Collectors must disclose the terms of the sale or transfer, including the nature of the data being transferred and the parties involved, to the Data Subject.
- Right to Negotiate Compensation: The Data Subject shall have the right to negotiate compensation for the transfer or sale of their Personal Data.
- Retention of Rights: All other rights of the Data Subject, including the right to review, edit, or remove their Personal Data, shall be retained after the transfer or sale.
Section 10: Effective Date This Act shall take effect six months after the date of enactment.
Section 11: Severability If any provision of this Act is found to be unconstitutional or invalid, the remaining provisions shall remain in effect.
Section 12: Review and Amendment This Act shall be reviewed every five years from the date of enactment and may be amended as necessary to address emerging privacy concerns and technological advancements.
As we navigate the complexities of the digital age, reimagining personal property rights to include data is essential. By granting individuals control over their own data and the right to profit from it, we can create a more equitable and transparent digital landscape. The proposed “Personal Data Ownership Act” serves as a crucial step in this direction, aiming to establish clear and enforceable rights for data subjects, ensuring that personal data is treated with the respect and value it deserves.
References
- Jurcys, P. (2019). Ownership of User-Held Data: Why Property Law is the Right Approach. Retrieved from Harvard Journal of Law & Technology.
- Ritter, J., & Mayer, A. (n.d.). Regulating Data as Property: A New Construct for Moving Forward. Retrieved from Duke Law & Technology Review.
- Global Perspectives on Digital Trade Governance. (2021). Data Ownership and Data Access Rights: Meaningful Tools for Promoting the European Digital Single Market? Retrieved from Cambridge University Press.
- Grimmelmann, J., & Mulligan, C. (n.d.). Data Property. Retrieved from American University Law Review.
- Käll, J. (2020). The Materiality of Data as Property. Retrieved from Harvard International Law Journal.
- Leonard, P. (2020). Beyond Data Privacy: Data “Ownership” and Regulation of Data-Driven Business. Retrieved from American Bar Association.
By considering the proposals and discussions in these resources, we can work towards a legal framework that ensures data ownership rights for all.

Fate, TX
CyberSquatting City Hall: How City Claimed a Developer’s Domain
How Fate registered a developer’s project domain after seeing it in official plans, then fought to keep that fact hidden
FATE, TX – Cities are expected to regulate development, not steal its name.
Records obtained by Pipkins Reports show the City of Fate registered the domain name of a private development, lafayettecrossing.com, while actively working with the developer who had already claimed that name in official plans. The move, made quietly during a heated approval process, raises serious questions about whether Fate’s city government crossed from partner to predator, taking digital ownership of a project it was supposed to oversee with neutrality and good faith… and depriving the developer of their rights to domain ownership.
What followed, attempts to conceal the purchase, shifting explanations from city officials, and a documented pattern of advocacy on behalf of the developer, suggests the domain registration was not an accident, but part of a broader effort to control the narrative around one of the most divisive projects in the city’s history.
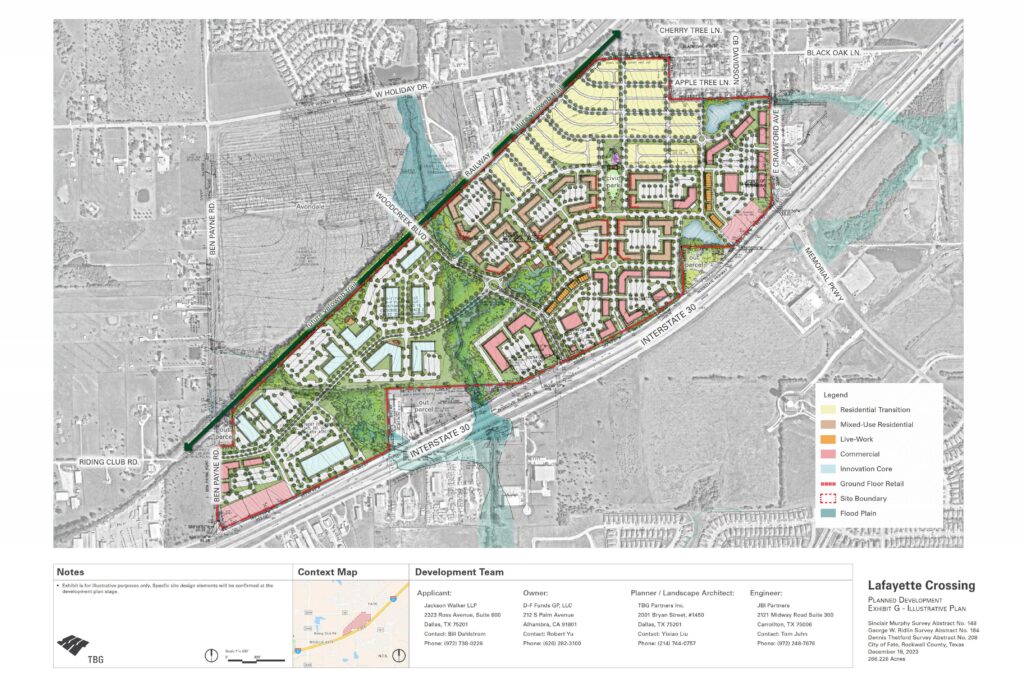
A site plan submitted by the developer, D-F Funds GP, LLC, led by Robert Yu, shows the project title “Lafayette Crossing” clearly identified in the title block on December 20, 2023. The document was part of the city’s official development review for the controversial project at the corner of I-30 and Highway 551.
Less than two months later, on February 7, 2024, the City of Fate registered the domain lafayettecrossing.com, Invoice #116953461, for $12.
Domain records confirm the registration date, with the domain set to expire on February 7, 2027. By that point, Lafayette Crossing was already the established name of the project, used by the developer and embedded in official plans circulating within City Hall.
This was not a coincidence. The city had the plans from the developer. Their were extensive talks regarding the project. Then the city registered the domain without the knowledge of the developer. This is known in the industry as, “Cybersquatting.”
The development, originally referred to as the “Yu Tract,” became known as Lafayette Crossing as it moved through the approval process. The project ignited intense public opposition over density, traffic congestion, infrastructure strain, and the long-term direction of Fate’s growth. Despite sustained resistance and packed council chambers, the city council approved the project.
The political fallout was severe. In the elections that followed, four council members and the mayor were replaced, an extraordinary level of turnover that reflected deep voter dissatisfaction. Two members from that Council, Councilman Mark Harper and Councilman Scott Kelley, remain, but are up for reelection this May.
That context matters, because the domain registration did not occur in isolation. It occurred amid a broader, documented pattern of city officials actively working to shape public perception in favor of the developer.
In February 2024, Pipkins Reports, then operating as the Fate Tribune, published an exposé based on internal city emails showing City Manager Michael Kovacs discussing strategies to “educate” the public about Lafayette Crossing. In those emails, Kovacs suggested deploying what he referred to as “Fire Support,” a term used to describe both paid and unpaid advocates brought forward to counter citizen opposition and astroturf public support for the project.
That reporting revealed a city government not merely responding to public concerns, but actively attempting to manage and counter them.
In a later publication, Pipkins Reports (Fate Tribune) documented the City of Fate’s hiring of Ryan Breckenridge of BRK Partners, engaging in what records showed to be a coordinated public relations effort aimed at improving the project’s image and swaying public sentiment. The campaign was presented as informational, but residents viewed it as advocacy on behalf of the developer, funded with public resources.
It was within this environment, where city staff had already aligned themselves publicly and privately with the developer’s interests, that the city registered the lafayettecrossing.com domain. Yet that fact remained hidden until PipkinsReports.com submitted an Open Records Request on September 30, 2025, seeking a list of all domains owned by the city.
Rather than comply, the City of Fate objected. On October 14, 2025, officials asked the Texas Attorney General’s Office for permission to withhold the records, citing “cybersecurity” concerns.
On January 6, 2026, the Attorney General rejected that claim and ordered the information released. The city complied on January 20, 2026.
In addition to the lafayettecrossing.com domain, the records revealed the city owns numerous domains tied to redevelopment and branding initiatives, including:
- FateTX.gov
- DowntownFate.com
- FateFoodHaul.com
- FateMainStreet.com
- FateStationHub.com
- FateStationMarket.com
- FateStationPark.com
- FateStationSpur.com
- OldTownFate.com
- TheHubAtFateStation.com
- TheSpurAtFateStation.com
- ForwardFate.com
Most clearly relate to city-led initiatives. LafayetteCrossing.com stands apart because it mirrors the established name of a private development already proposed, named, and publicly debated.
When questioned via email, Assistant City Manager Steven Downs initially suggested the domain purchase occurred long before his involvement and downplayed any potential issues. When we revealed documents to show Downs was actively engaged with the project at the same time the Lafayette Crossing name entered the city’s official workflow, his story changed.
In follow-up correspondence, Downs acknowledged he was aware of the project name, while placing responsibility for the domain purchase on former Assistant City Manager Justin Weiss. Downs stated he did not know whether the developer was aware of the purchase and said he was not concerned about potential liability.
What remains unexplained is why the city registered the domain at all, knowing it belonged to a private project, and why it attempted to keep that information from the public.
Opinion
Viewed in isolation, a $12 domain purchase might seem trivial. Viewed in context, it is not.
When a city that has already worked to astroturf support, hire public relations firms, and counter citizen opposition also quietly registers a developer’s project domain, then attempts to conceal that information from the public, the line between regulator and advocate disappears.
The question is no longer whether the city knew the name. The record shows it did.
The question is why a city government so deeply invested in selling a controversial project to its residents felt the need to take ownership of the project’s digital identity as well.
Control of messaging, control of perception, and control of narrative are powerful tools. Sometimes it is equally as important to control what is not said.
Election
New Poll Shows Crockett, Paxton Leading Texas Senate Primary Contests

Texas Senate Primaries Show Early Leads for Crockett and Paxton
AUSTIN, Texas – A new poll released by The Texas Tribune indicates that Jasmine Crockett and Ken Paxton are leading their respective primary races for the U.S. Senate seat in Texas. The survey, published on February 9, 2026, highlights the early momentum for both candidates as they vie for their party nominations in a closely watched election cycle. The results point to strong voter recognition and support for Crockett in the Democratic primary and Paxton in the Republican primary.
The poll, conducted among likely primary voters across the state, shows Crockett holding a significant lead over her Democratic challenger James Talarico, while Paxton maintains a commanding position among Republican contenders John Cornyn & Wesley Hunt.
According to the poll, Ken Paxton leads with 38 percent of likely GOP primary voters, pulling ahead of incumbent John Cornyn, who trails at 31 percent, while Wesley Hunt remains a distant third at 17 percent. The survey indicates Paxton would hold a commanding advantage in a runoff scenario and currently outperforms Cornyn across nearly every key Republican demographic group, with Latino voters the lone exception, where Cornyn maintains a seven-point edge.
Among Democrats, the poll shows Jasmine Crockett opening a notable lead, capturing 47 percent of likely primary voters compared to 39 percent for James Talarico—a meaningful shift from earlier polling that had Talarico in the lead. While still early, the numbers suggest momentum is consolidating ahead of primaries that will determine the general election matchups.
Jasmine Crockett, a sitting U.S. Representative whose district lines were redrawn out from under her, has responded to political extinction with a desperate lurch toward the U.S. Senate. Her campaign, widely criticized as race-baiting and grievance-driven, has leaned heavily on inflaming urban Democratic turnout while cloaking thin policy substance in fashionable slogans about healthcare and “equity.”
By contrast, Ken Paxton enters the race with a long, battle-tested record as Texas Attorney General, earning fierce loyalty from conservatives for his aggressive defense of state sovereignty, constitutional limits, and successful legal challenges to federal overreach. Though relentlessly targeted by opponents, Paxton’s tenure reflects durability, clarity of purpose, and an unapologetic alignment with the voters he represents—qualities that define his standing in the contest.
The Texas U.S. Senate race draws national attention, as the state remains a critical battleground in determining the balance of power in Congress. With incumbent dynamics and shifting voter demographics at play, the primary outcomes will set the stage for a potentially contentious general election. The Texas Tribune poll serves as an initial benchmark, though voter sentiment could evolve as campaigns intensify and debates unfold in the coming weeks.
Featured
Kristi Noem Commemorates Border Crossing Decline with National Leaders

WASHINGTON, D.C. – Secretary of Homeland Security Kristi Noem joined national security leaders in a dual-state event to commemorate a historic decline in border crossings, according to an official release from the Department of Homeland Security. The event spanned two locations, Arizona and North Dakota, in a single day, highlighting coordinated efforts to strengthen border security. Noem, alongside other officials, marked the achievement as a significant milestone in national security policy.
The Department of Homeland Security reported a measurable drop in unauthorized border crossings, attributing the success to enhanced enforcement measures and inter-agency collaboration. Specific data on the decline was not detailed in the initial announcement, though officials emphasized the impact of recent policy implementations. The two-state commemoration underscored the geographic breadth of the issue, addressing both southern and northern border concerns.
In Arizona, Noem and security leaders reviewed operations along the southern border, a longstanding focal point for immigration enforcement. Later in the day, the group traveled to North Dakota to assess northern border security, an area often overlooked in national discussions but critical to comprehensive policy. The dual focus aimed to demonstrate a unified approach to protecting all U.S. borders, per the department’s statement.
The official release from Homeland Security included remarks from Noem, who praised the dedication of personnel involved in the effort. “This decline in crossings is a testament to the hard work of our agents and the effectiveness of our strategies,” she said. Her comments were echoed by other leaders present, though no additional direct quotations were provided in the initial report.
Background on the border security initiatives reveals a multi-year push to address vulnerabilities at both entry points. Southern border challenges, particularly in Arizona, have long dominated policy debates due to high volumes of crossings and complex terrain. Meanwhile, northern border issues in states like North Dakota often involve different dynamics, including trade security and seasonal migration patterns. The Department of Homeland Security has prioritized resources for both regions, though specific funding allocations remain undisclosed in the latest update.
The cause of the reported decline ties directly to recent enforcement actions, though exact mechanisms were not specified in the announcement. Officials pointed to improved technology, increased staffing, and stronger partnerships with local and state authorities as contributing factors. Further details on these efforts are expected in forthcoming reports from the department, which has committed to transparency on border metrics.
Opinion
The recognition of a decline in border crossings signals a potential turning point in how the nation secures its frontiers. Celebrating this achievement in two distinct regions reinforces the importance of a comprehensive strategy that does not neglect less-discussed areas like the northern border.
Events like these also serve as a reminder that security is not a partisan issue but a fundamental duty of government. Prioritizing resources and personnel to protect sovereignty while maintaining lawful entry processes should remain a core focus, ensuring that progress is sustained through consistent policy and accountability.
You must be logged in to post a comment Login